cara adapter wifi laptop bisa membaca semua jaringan wifi

Title: Cara Mengatasi Wifi Tidak Terdeteksi, Hilang, atau Tidak Muncul di Laptop
Channel: Sobat OPS
Cara Mengatasi Wifi Tidak Terdeteksi, Hilang, atau Tidak Muncul di Laptop by Sobat OPS
Unlock ALL Hidden Wi-Fi Networks: Your Laptop's Secret Weapon!
Unveiling the Invisible: Master Your Laptop's Wi-Fi Powers!
Have you ever wondered about those mysterious, unseen Wi-Fi networks lurking in the digital shadows? They’re there, whispering secrets, but often hidden from your view. Your laptop, however, holds the key. It's a secret weapon against these invisible signals. Let's embark on a journey to unlock their potential.
Decoding the Digital Veil: What Are Hidden Networks?
Hidden networks are those that broadcast their presence selectively. Instead of displaying a friendly name (SSID), they remain invisible. They operate in stealth mode. This can be for various reasons. Some users might hide their network for added security. Others simply prefer privacy. You may not see them in your list of available connections.
However, this doesn't mean they are truly inaccessible. Your laptop is a powerful tool. It can be expertly used to detect these networks. Knowing how is a valuable skill in today's connected world. The process empowers you to gain insights into the digital landscape surrounding you.
The Laptop's Arsenal: Tools of the Trade
Your laptop is equipped with the tools to find these hidden networks. Firstly, your built-in Wi-Fi adapter is the primary instrument. It can scan for signals. Secondly, the operating system offers built-in utilities. These tools let you manage your network connections. Finally, there are third-party applications. These offer enhanced features.
Consider the command prompt or terminal. It's a gateway to network information. You can use it to scan for networks. You can also configure specific settings. These steps provide you with the necessary data. Remember, explore these options. Experiment and familiarize yourself with your laptop’s capabilities.
Unmasking the Invisible: Step-by-Step Guide
Here’s how to reveal hidden Wi-Fi networks. The first step involves accessing your network settings. Navigate to your Wi-Fi settings in your operating system. Next, look for an option to "Add a network" or "Manually connect." You’ll need to provide the network's exact name (SSID). You might also need its security type.
Next, choose the correct security protocol (e.g., WPA2, WEP). After that, type in the network’s password. This is also called the "passphrase." Therefore, double-check the information before you continue. If you have the right credentials, your laptop should connect. You can also use Wi-Fi analyzer apps. These offer simple network discovery.
Security Considerations: Proceed with Caution
Understanding hidden networks is critical. However, it's important to respect privacy. Only attempt to access networks you are authorized to use. Always prioritize ethical and legal considerations. Never try to hack into a network. It's also crucial to be aware of potential security risks. Connecting to unknown networks can expose your device to threats.
Consequently, use a reliable antivirus. Maintain your computer’s firewall. Be mindful of the data you transmit. Because you want your information safe. Also, think about using a VPN. It will offer added security.
Beyond the Basics: Advanced Techniques
Beyond the standard methods, explore more advanced approaches. Consider using command-line tools. For example, “netsh wlan show networks mode=BSSID” is a Windows command. It can provide detailed information about nearby networks. The output unveils the hidden SSIDs.
Alternatively, Wi-Fi analyzers provide in-depth analysis. They can reveal channels. They also highlight signal strength. These tools are especially useful. They provide valuable insights into network performance. So, learn to read network signal strength.
Troubleshooting: When Things Go Wrong
Sometimes, you may encounter issues. You may be unable to connect to a hidden network. First, double-check the SSID spelling. Ensure you've entered the correct password. Verify the security protocol is correct. For the most part, the network’s settings might be incorrect. This could cause connectivity problems.
Check your driver settings. Make sure your Wi-Fi adapter driver is updated. Try restarting your laptop and your router. This often resolves minor glitches. If problems persist, research solutions online. You'll find helpful forums and guides.
The Power of Knowledge: Your Digital Advantage
Now, you possess valuable knowledge. You know how to find hidden Wi-Fi networks. Furthermore, you know how to avoid the risks. You can leverage this skill in many ways. You can troubleshoot connection issues. You can also optimize your own network settings. Ultimately, this knowledge gives you power.
It empowers you in the digital realm. So, embrace this knowledge. Stay informed about evolving technologies. Explore more about network security. Never stop learning. It's a continuous journey.
**HP Ubuntu 18.04 WiFi Fix: Download Drivers NOW!**Unlock ALL Hidden Wi-Fi Networks: Your Laptop's Secret Weapon!
Hey tech enthusiasts! Ever wonder what's REALLY lurking in the Wi-Fi shadows? You know, those networks hiding in plain sight, whispering secrets you can't quite hear? Well, buckle up, because we're about to arm your trusty laptop with the ultimate secret weapon: the ability to sniff out and connect to all those hidden Wi-Fi networks. Think of it as giving your laptop superpowers, turning it into a digital detective ready to crack the case of the invisible internet. Let's dive in!
1. The Wi-Fi Graveyard: Why Are Networks Hidden in the First Place?
Before we get to the good stuff, let's unravel the mystery of why these Wi-Fi networks even bother hiding. It's not always some nefarious plot, I promise! Sometimes, it's simply about security. Hiding the network's name (SSID) can make it slightly harder for casual snoopers to find and connect. Think of it like putting a lock on your digital front door. Other times, networks are hidden for specific devices or smart home applications, ensuring they don't clutter the Wi-Fi landscape. It's like a private backstage pass, just for the chosen few. It's also about controlling access, preventing unwanted users from hogging bandwidth.
2. Understanding Your Wireless Arsenal: The Tools of the Trade
So, how do we equip ourselves for this digital treasure hunt? We're not talking about James Bond gadgets here (though wouldn't that be fun?). We'll be using tools readily available on your laptop, and sometimes, a little software power-up. Think of it like having a Swiss Army knife for Wi-Fi. But before we get to specifics, let's clarify that we are not intending to exploit anyone's network without proper authorization as that is unlawful.
3. Your Laptop's Built-In Spyglass: Using Your Operating System
Did you know your computer already has a built-in capability to scan for available Wi-Fi networks, including the hidden ones? Let's start with the basics. We'll be diving into the settings of your operating system. For Windows users, this means opening the Network and Internet settings, then clicking on "Change adapter options." macOS users, on the other hand, can find these settings under System Preferences > Network. From here you are likely to be able to see a list of available Wi-Fi networks, and many operating systems will show hidden ones.
4. Decoding the Whispers: Identifying Hidden Networks on Windows
Okay, Windows users, here's the lowdown. Often, you’ll see an option to 'Connect to a hidden network.' This is your golden ticket! Click on it, and you will be prompted for the network name (SSID), security type, and security key. You got the network name and the password? Type it in, and voila! You're connected.
5. Mac Mavericks: Unearthing Hidden Networks with Ease
macOS is just as sleek and stylish in revealing hidden networks. Typically, you want to go to your Wi-Fi icon in the menu bar. Select "Join Other Network…" and enter the name of the hidden network and the password. It's usually that simple. Now you're ready to explore.
6. Level Up: Software Solutions for Hidden Network Detection
Sometimes, the built-in tools aren't quite enough. That's where third-party software comes in. They're like specialized lenses for your digital spyglass, giving you a clearer view.
7. The Power of Wireless Network Analyzers: A Deeper Dive
Wireless network analyzers are like high-tech radar systems for your Wi-Fi connection. They can scan the airwaves and uncover a wealth of information, including the hidden network names, channels being used, and the security protocols. A great example is Wi-Fi Analyzer. It is an android application, that allows you to view all the information regarding the surrounding wireless networks.
8. The Security Symphony: Understanding Wi-Fi Encryption Types
Before you start connecting to just any network, let's talk security. It's like choosing the right lock for your door. You need to know your WEP, WPA, and WPA2/3 encryption. WEP is the old, weak lock. WPA is better, but WPA2/3 are the latest and strongest, offering you the best protection.
9. Connecting the Dots: Entering the Hidden Network Details
Once you've identified a hidden network's name (SSID) and security type, it's like putting the pieces of a puzzle together. You'll need to manually enter this information into your Wi-Fi settings. This is where the information found by your applications or operating systems comes into play.
10. Common Pitfalls and Troubleshooting: Navigating the Wi-Fi Maze
Sometimes, things don't go as planned. Wi-Fi can be a fickle beast. Encounter an issue? It is normal. Double-check the SSID and password. Make sure your device is within range. Check if the network is blocking your MAC address. If you are having trouble, take a deep breath (seriously!) and start again. Like trying to find a hidden treasure, sometimes you need to go back to the drawing board.
11. Ethical Considerations: Respecting Network Boundaries
Here's the most important part: We’re all about uncovering information, not exploiting it. Always, always, obtain permission before connecting to a network that isn't yours. This is not about being a digital bandit; it's about understanding how things work.
12. Boosting Your Wi-Fi Signal: Fine-Tuning Your Connection
Even if you have found a network, a weak signal can ruin the experience. Position your laptop strategically. Reduce obstructions. Consider a Wi-Fi extender or a more powerful router if needed.
13. Beyond the Basics: Advanced Techniques for the Curious
Once you have mastered the basics, you can move to more advanced techniques such as packet sniffing and analyzing network traffic. Such techniques are for the truly tech-savvy.
14. Protecting Yourself: Security Best Practices for Hidden Networks
When connecting to any network, including hidden ones, always use a strong password, and enable firewalls and anti-virus software. Secure all of your devices. Be wary of public networks.
15. The Future of Wi-Fi: What's Next?
Wi-Fi technology is constantly evolving. Newer standards like Wi-Fi 6 and 6E promise even greater speeds and efficiency. Keep up with these changes. Stay curious. Your laptop is your secret weapon, and the world of Wi-Fi is constantly evolving.
Closing Thoughts:
So there you have it! We've peeled back the layers of the hidden Wi-Fi world. You are now equipped with the knowledge and tools to unlock and connect to all the silent networks around you – provided you have the necessary permission, of course! Remember, this isn't about breaking the rules, it's about understanding the technology that surrounds us. Now go forth, explore, and be a responsible digital explorer!
Frequently Asked Questions (FAQs)
1. Is it illegal to connect to a hidden Wi-Fi network?
It could be, If you do not have the permission to do so. Connecting to a network without authorization is generally considered a form of trespassing, can violate local laws and may have significant legal implications.
2. What if I can see the hidden network but can't connect?
Double-check the network name and password. Also, ensure you're in range. The network may be restricting you by something like MAC address filtering.
3. Do hidden networks offer better security?
Not inherently, but hiding the SSID can deter casual snoopers. The level of security depends on the encryption used (WPA2/3 is best).
4. Can I use this to hack Wi-Fi?
We want to make it clear that it is unlawful. This is about understanding networks, not exploiting them.
5. What if I forget the network password?
If you are the owner of the network, you can reset the router. If you are on a network you do not own, you'll need to ask the owner for help.
1) Principal Keywords: Hidden Wi-Fi Networks, Laptop.
2) SEO Headline: Hidden Wi-Fi Networks: Your Laptop's Secret Weapon!
3) Pathway: Hidden Wi-Fi Guide
4) Meta Summary: Unlock hidden Wi-Fi networks with your laptop! Discover how to find and connect, explore security, tips and tricks. Learn how to become a Wi-Fi detective!
5) Image Alt Text: Laptop scanning for hidden Wi-Fi networks.
Laptop WiFi Freedom: Ditch the Cafés, Own Your Connection!Cara atasi WiFi tidak bisa connect di laptop not connected
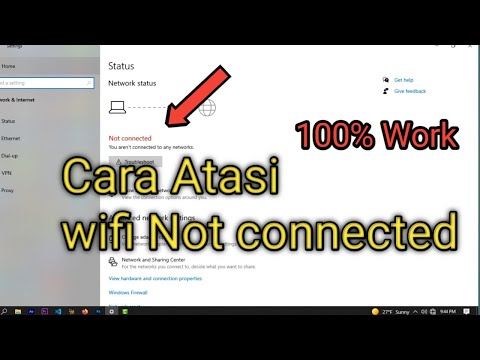
By ijal tutorial Cara atasi WiFi tidak bisa connect di laptop not connected by ijal tutorial
Cara Mengatasi Jaringan WIFI Tidak Terdeteksi di Laptop atau Komputer

By LANGIT MERAH TUTORIAL Cara Mengatasi Jaringan WIFI Tidak Terdeteksi di Laptop atau Komputer by LANGIT MERAH TUTORIAL
Cara Mengatasi Adapter Wifi Yang Hilang di Windows 10 Pc atau laptop

By WINTECH id Cara Mengatasi Adapter Wifi Yang Hilang di Windows 10 Pc atau laptop by WINTECH id

Title: Cara mengganti wireless network adapter pada laptop
Channel: Rupa Rupi Rdua
Cara mengganti wireless network adapter pada laptop by Rupa Rupi Rdua
My Laptop Work
Unlock ALL Hidden Wi-Fi Networks: Your Laptop's Secret Weapon!
We live in a world constantly bathed in the invisible hum of wireless signals. From the coffee shop down the street to the bustling airport terminal, Wi-Fi permeates our existence. Yet, often, we're only privy to the tip of the iceberg—the networks bravely broadcasting their presence for all to see. What about the hidden networks, the furtive signals whispering secrets just beyond our laptop's normal view? This article unveils the strategies and techniques to transform your laptop into a powerful reconnaissance tool, allowing you to discover and connect to all Wi-Fi networks, even those deliberately concealed.
Understanding the Invisible: Why Hide a Wi-Fi Network?
Before diving into the how, it's crucial to understand the why. Why would someone choose to hide their Wi-Fi network in the first place? While it might seem counterintuitive, there are several legitimate reasons.
- Security through Obscurity: Hiding a network's SSID (Service Set Identifier, or network name) makes it slightly less vulnerable to casual sniffing. It doesn't provide airtight security, but it can deter less sophisticated attackers and automated scripts.
- Targeted Access: Businesses or individuals might hide their network and then provide the SSID and password to specific users or devices. This is a common practice for guest networks, ensuring only authorized devices can connect.
- Avoiding Interference: In densely populated areas, multiple Wi-Fi networks can interfere with each other, leading to slower speeds and connectivity issues. Hiding the SSID can help a network "fly under the radar," reducing the likelihood of interference.
- Privacy: Some users simply prefer to keep their network private, wanting to avoid unwanted attention or accidental connections from neighbors.
It's important to reiterate that hiding a network mostly provides a minor layer of security, and it is not airtight. However, understanding the motivation behind hidden networks helps us grasp the methods needed to discover them.
Your Laptop: The Key to Unlocking Hidden Networks
Your laptop, often underestimated in its power, is more than just a device for browsing the web and checking emails. It's a versatile tool, capable of performing tasks that surpass simple tasks. With the right software and a little know-how, your laptop can become a Wi-Fi network detective.
1. The Wireless Adapter Conundrum
Your laptop's built-in wireless adapter is the primary interface to the wireless world. Its capabilities determine the features available to you when attempting to crack the Wi-Fi network. Make certain that your adapter supports different modes.
- Monitor Mode: This mode allows your adapter to passively "listen" to all Wi-Fi traffic without associating with a specific network. This is essential for capturing information like the SSID (even if hidden) and other network data. Many modern wireless adapters support this mode natively, while others might require driver updates or external tools.
- Packet Injection: Being able to inject packets means you can transmit data into the wireless network. This is crucial for carrying out attacks to discover the hidden networks.
2. Software Arsenal: Tools of the Trade
Several software tools can help you discover hidden Wi-Fi networks. The best choice frequently hinges on your operating system (OS).
- For Windows Users:
- NetStumbler (Older, but still useful): A classic Wi-Fi scanner for Windows. While its interface may look dated, NetStumbler remains a reliable tool for identifying hidden networks, MAC addresses, and signal strengths.
- Acrylic Wi-Fi Professional: A more advanced, modern Wi-Fi scanner with a sleek interface. It offers numerous details on the network, including the SSID (even hidden) and related information.
- Wireshark: While primarly a network protocol analyzer, Wireshark is a powerful tool. By using the correct filters, we can sniff the network for data.
- For macOS Users:
- WiFi Explorer: A fast and intuitive Wi-Fi scanner with a user-friendly interface. WiFi Explorer provides detailed information about nearby networks, including those hidden.
- Airport Utility (Built-in): macOS has a somewhat hidden utility to give you a comprehensive overview of the network.
- Terminal and Command-Line Utilities: macOS comes with powerful command-line tools such as
airportandtcpdump, which allow you to gather detailed information about Wi-Fi networks.
- For Linux Users:
- Airmon-ng (part of the Aircrack-ng suite): The cornerstone of many Linux-based Wi-Fi auditing toolsets. Airmon-ng puts your wireless adapter into monitor mode, enabling you to capture network traffic.
- Kismet: A flexible wireless network detector, sniffer, and intrusion detection system. Kismet excels at passively capturing data, identifying hidden networks, and identifying active clients.
- iwconfig/iwlist: These command-line utilities are part of the core Linux networking tools. They provide a wealth of information about wireless interfaces.
3. The Art of the Passive Scan: Unveiling Hidden Names
The simplest and often most effective method for discovering hidden networks is the passive scan. This technique involves listening for network beacons without actively probing for them. These beacons are short data packets broadcast periodically by Wi-Fi access points, including the network name (SSID). Even if the SSID is hidden, the access point must still broadcast these beacons to announce its presence and allow devices to connect.
- Using Wi-Fi Scanners: Open your chosen Wi-Fi scanner (NetStumbler, Acrylic Wi-Fi, WiFi Explorer, etc.). In a default scan, even hidden networks will often appear. The scanner will reveal the BSSID (MAC address of the access point) and the channel it's operating on.
- Command-Line Magic (Linux):
- Put your wireless interface into monitor mode using
airmon-ng start wlan0(replacewlan0with the name of your wireless interface). - Use
airodump-ng wlan0mon(oriwlist wlan0mon scanif you are not utilizing theaircrack-ngsuite). This command will display a list of all detected Wi-Fi networks, including those with hidden SSIDs. Look for entries where the ESSID is blank.
- Put your wireless interface into monitor mode using
4. The Active Reconnaissance: Probing for Answers
Sometimes, a passive scan alone isn't enough. Hidden networks may be configured to broadcast beacons less frequently or to use more sophisticated security measures. In such situations, you may need to employ active reconnaissance techniques.
- Deauthentication Attacks (Ethical Use Only!): This method involves sending deauthentication packets to connected clients on a target network. When a client is deauthenticated, it attempts to reconnect, revealing the hidden SSID during the reconnection process. Use this technique ethically and with proper authorization.
- Use
aireplay-ng -0 10 -a [BSSID] -c [client MAC address] wlan0mon(Aircrack-ng suite)-0: Deauthentication attack10: Number of the attack packets to send.-a [BSSID]: Target network's BSSID.-c [client MAC address]: Target client MAC address.wlan0mon: Monitor mode interface.
- Monitor the traffic as the client attempts to reconnect, revealing the hidden SSID.
- Use
- Packet Injection (for Advanced Users): By injecting probe requests, you can actively request the hidden SSID from the access point. This requires a deeper understanding of wireless networking and packet manipulation.
- You will need a tool like Scapy, a powerful Python-based packet manipulation tool.
- Craft a probe request packet with the target network's BSSID in it.
- Inject the packet using your wireless adapter in monitor mode.
- Capture the response from the access point, which should contain the hidden SSID.
5. Connecting to the Hidden Network: The Final Step
Once you've revealed the hidden SSID, connecting to the network is usually straightforward.
- Windows:
- Open the Network and Sharing Center.
- Click "Set up a new connection or network."
- Choose "Manually connect to a wireless network."
- Enter the SSID (the hidden network's name), security type (WEP, WPA, WPA2, etc.), and the password.
- Click "Connect".
- macOS:
- Click the Wi-Fi icon in the menu bar.
- Choose "Join Other Network…"
- Enter the SSID, security type, and password.
- Click "Join."
- Linux:
- Use the command line or a network manager like NetworkManager.
- Edit the network configuration.
- Enter the SSID, security type, and password.
- Save and connect.
Ethical Considerations and Legal Boundaries
It's imperative to use these techniques responsibly and ethically.
- Never access a network without permission. Doing so is illegal and can have serious consequences.
- **Use these techniques for
